Thank You for the tip!
I was wondering about what was causing this. I managed to figure out right click > save link as, but got a little worried when I saw it was blocked and flagged as insecure, especially when I didn’t see any signed checksum files. Am I just too paranoid?
Anyways, it’s a cakewalk compared to Debian. But I suppose that’s not saying much lol.
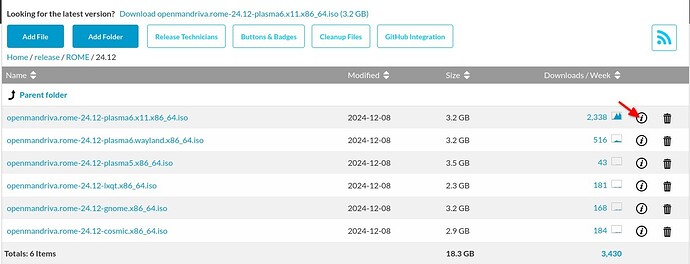
I must have got luky on my fist try because i hit download now and was taken to souceforge and the download started automatically. However things did get complicatded when i needed to try other isos. Can anyone point me to a server iso i’m having problems with rome plasma and want to try installing manually from a server iso to see if that reproduces the problem.
Try installing Plasma6 slim iso instead. I do not believe the latest server installers for ROME are ready yet. They weren’t a high priority because they weren’t used much. Seems we may be changing in that regard.
If there were server installers they would be here.
Brave here as well. I had to right click on the iso file and click “save link as” and then it just stopped.
HOWEVER, click on the Dowload button at the top right of the browser and it says “insecure download blocked.”
Click on the download file and then click “download insecure file.”
It explains a lot. I checked all distro ISOs downloaded and can confirm they’re from HTTPS links. OpenMandriva was the only one that refused to download on Brave. I was forced to go to your SourceForge page and had no issue downloading there since it’s HTTPS-hosted.
So I 100% agree that HTTP is likely the issue. Configuring ISO links with HTTPS should solve this. It should’ve been set up like this from the start but hey at least we know now ![]()
One suggestion - have more torrent options available. This will save enormous bandwidth.
If I get the torrents I will seed endlessly
The only torrents I saw were old. I could have been in the wrong place. It wasn’t straight forward.
The bigger problem is perhaps that the process is not complicated enough. There doesn’t seem to be any signatures to verify, and so users cannot ensure the provenance of the files. Please correct me if I am wrong.
Found the same one and downloaded it at first not realizing at first it was from 2023.
If from sourceforge (example)
OpenMandriva Lx - Browse /release/ROME/24.12 at SourceForge.net
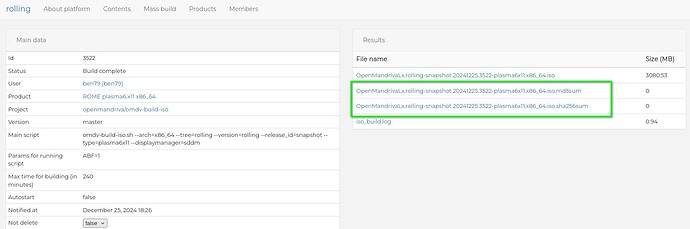
If from abf containers (example)
https://abf.openmandriva.org/platforms/rolling/products/73/product_build_lists/3522
right click, Save file with name - or what your browser shows.
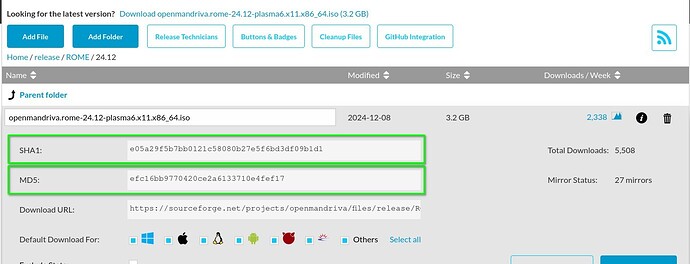
I wasn’t actually talking about checksums, but PGP signatures. A matching SHA proves that the file downloaded properly, but it doesn’t prove that it is the right file, as it is possible that the iso and the SHA file were compromised on the file server. This has happened to distros before, Mint being a famous example. Linux Mint Hacked Briefly – Bad ISOs, Compromised Forum | Hackaday
Here is Debian’s answer to the problem: Verifying authenticity of Debian images
Are you making the argument that a user should check multiple download sources to ensure that they all have the same checksum? That would work, even if it isn’t optimal, but you definitely need to detail that process very clearly as it is not expected.
Here is a blog post (not mine) by a fellow who explains the problem with using checksums for verification. Backdoored Linux Mint, and the Perils of Checksums | Micah Lee
One way to fix the problem properly would be to sign your sha256sum file with a key that you have email verified (with an email address from the openmandriva domain, say “security or release @ openmandriva.org”) with keys(dot)openpgp(dot)org. Then a user who downloads your sha256sum file would be able to download your email verified public key from openpgp and verify the sha256sum file, and thereby verify that the iso file is legitimate. The email verification on openpgp.org helps because while you can spoof a sending address, openpgp.org sends out an email with a verification code, and having received it strongly implies ownership of the domain.
@encw ok I misunderstood your question. Sorry.
No problem! While we’re on the topic; does OpenMandriva host its own repositories? And is dnf configured properly to check package signatures? The fact that the download iso itself is not signed leads me to believe that the repository system might also be unsigned, and therefore be a security weakness.
Please take a look at the “Important” section highlighted with purple. DNF :: Fedora Docs
You need to ask a developer.
Edit: Excuse me, developers may see this post but no guarantee. OM-Chat may be quicker. Edit some more: You may have a valid point.
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.